You are here
The true value of a WAF in the digital world
Web applications and web API remain privileged targets for cyber criminals. Vulnerabilities are still too often introduced during the development and deployment of applications, leaving your valuable information, such as personal data or credit card information exposed.
Implementing a Web Application Firewall (WAF) solution provides the right answer to mitigate these risks and protect your web services and valuable data from sophisticated cyber-attacks.
However, a WAF implementation remains a complex task for many IT or Security teams. In many cases, organisations end-up with a WAF partially open to keep their application available, significantly limiting the return on investment and the level of security initially promised.
Your Benefits
- Get your web applications efficiently protected – 100% of our deployments run in blocking mode
- Minimal license cost & optimal investment - Pay for our expertise
- Agile and flexible deployment model suited to your environment
- Lower the number of false positives and augment operational efficiency of your security team.
- A direct access to our experts in case of problem, we are here to help you
- Stay focused on your core business with our full managed services
Our Solutions
Drawing on 20+ years of cyber security expertise and WAF profiles development, our WAF Application Intelligence™ solution provides proven, simple, and effective security to meet your needs in every situation – from SMB companies searching for a fully managed solution to big accounts with complex management challenges.
The Approach WAF AI solution is the perfect fit for any of the following use cases:
- Small and Medium Businesses (SMB): You don’t have the right resources (human and financial) to implement and manage a WAF to effectively block attacks.
- Critical Applications with sensitive data: Your data needs a higher level of protection than generic rules targeting common patterns.
- Large-scale environment (on-premises or in the cloud) managing more than 100 applications: Efficiently securing all your web applications is too expensive or too complex.
- Bundling a WAF solution with your developed application/API: Including a portable software-version only WAF into your product distribution, tightly protecting your software.
- Compliance with regulations such as PCI-DSS: You need support to ensure your business is compliant with all current rules and regulations.
Our technology
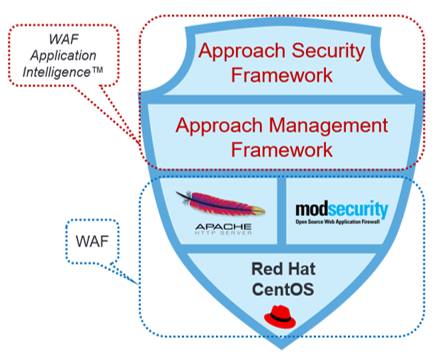
Our solution is built on open-source technologies and empowered with our Security and Management Framework. It is designed and continuously improved to stop the most sophisticated and recent cyber-attacks. It is compliant with PCI-DSS and designed to mitigate out-of-the-box the OWASP Top 10 (application & API) and SANS Top 25 vulnerabilities.
The features
The Approach WAF AI offers tall security features expected by the market, built-in to our framework by default.
Different business expectations require different levels of security and support – that’s why we developed 2 editions.
 Advanced Edition |  Standard Edition | |
|---|---|---|
 Security Features Security Features | ||
| Approach Security Framework | ✔ | ✔ |
| Approach Management Framework | ✔ | ✔ |
| Safe Defaults | ✔ | ✔ |
| Full control on white listing | ✔ | — |
 Deployment Deployment | ||
| Multi-environment | ✔ | ✔ |
| Redundant & Scalable | ✔ | ✔ |
| Easy 3rd party integration | ✔ | — |
| Transparent and open | ✔ | — |
 Full Managed services Full Managed services | Optional | Optional |
- The “Advanced Edition” is intended for datacentres and large companies. It is entirely customizable and aims to be tightly integrated in your environment with your own technologies. This version is preconfigured with the “safe defaults” philosophy and white listing must be explicitly activated.
- The “Standard Edition” is a standalone virtual machine, with pre-activated security rules that will allow most common traffic. The operating system and the core components cannot be modified.
Both versions contain pre-activated security rules that allow only the most common traffic.
We offer the option of ‘full managed services’ in which case Approach manages the WAF and ensures it stays up-to-date, so you are free to focus on your core business.
Our services
We strongly believe that any WAF solution must be delivered with a minimum level of service to provide the best possible outcome and maximum security.
Why choose us?
- Solution built on our 20+ years cyber security expertise
- Proven successes in critical environments: NATO, LuxTrust, Bpost, various banks, Connective, … Not a single security breach in 20 years!
- Open-source technologies
- Our WAF experts and SOC analysts are also our Ethical hackers, with deep knowledge of web applications attack methods and vulnerabilities
- Compliance PCIDSS – OWASP Top 10 – SANS 21/25
- 100% of our PoC are converted into customer projects








